Introduction
SentryPC is a powerful computer monitoring and control software designed for businesses, educational institutions, and parents. With its comprehensive features, including activity monitoring, content filtering, time management, and remote management capabilities, SentryPC enables users to track and manage computer usage effectively. Whether you’re seeking to enhance productivity in the workplace, enforce internet usage policies in educational settings, or ensure a safe online environment for your family, SentryPC offers a solution tailored to your needs.
Pricing
Pricing is a crucial factor to consider when selecting a monitoring solution like SentryPC. Understanding the pricing structure, including any additional costs or discounts, is essential for making an informed decision. In this section, we’ll explore SentryPC’s pricing model and compare it with similar products in the market.
SentryPC Pricing Model:
SentryPC offers flexible pricing plans designed to accommodate various user needs and budgets. The pricing model typically consists of different subscription tiers, each offering a unique set of features and benefits. Users can choose a plan that best aligns with their monitoring requirements and financial constraints.
Subscription Options:
- Monthly Plans: SentryPC often provides monthly subscription options, allowing users to pay a fixed amount on a month-to-month basis. This option offers flexibility, allowing users to cancel or modify their subscription as needed.
- Annual Plans: For users seeking long-term monitoring solutions, SentryPC may offer discounted annual subscription plans. These plans often provide cost savings compared to monthly subscriptions and may include additional features or benefits.
Tiered Pricing Structure:
SentryPC’s pricing tiers typically vary based on factors such as:
- Features: Higher-tier plans may offer more advanced features and capabilities, such as enhanced monitoring tools, increased storage capacity, or additional support options.
- Device Coverage: The number of devices covered by each plan may vary, with higher-tier plans accommodating more devices for monitoring purposes.
- Subscription Duration: The duration of the subscription (monthly or annual) may affect the overall pricing, with annual plans often offering discounted rates compared to monthly subscriptions.
Comparison with Competitors:
When evaluating SentryPC’s pricing, it’s essential to compare it with similar products in the market. Factors to consider in this comparison include:
- Feature Parity: Assess whether SentryPC‘s pricing is competitive relative to other monitoring solutions offering similar features and capabilities.
- Value Proposition: Evaluate the overall value proposition of SentryPC’s pricing, taking into account factors such as customer support, ease of use, and reliability.
- Total Cost of Ownership: Consider the total cost of ownership over time, including any additional fees, upgrade costs, or hidden charges associated with SentryPC and its competitors.
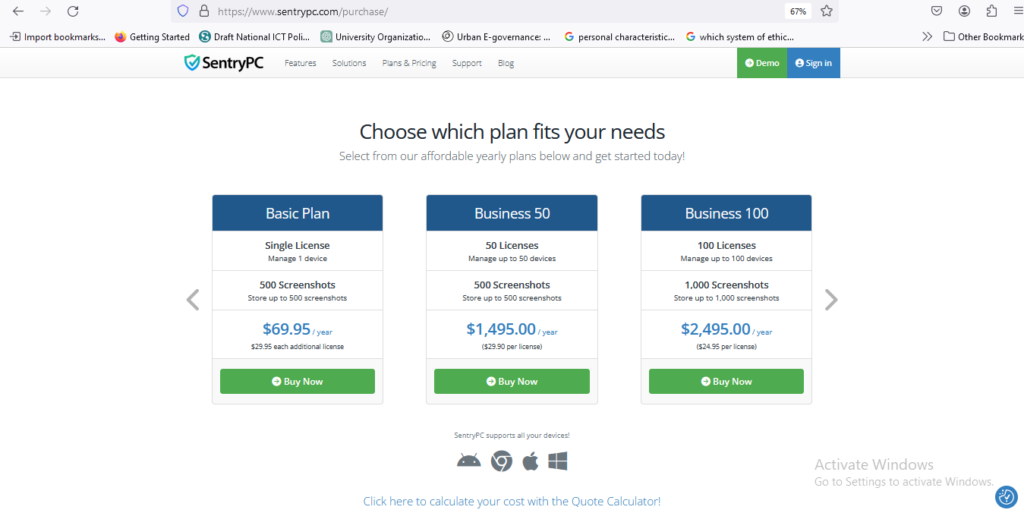
- Pricing Plans: Include screenshots or visual representations of SentryPC’s pricing plans, showcasing the different tiers and corresponding features.
- Comparative Pricing Table: Create a comparative pricing table that illustrates SentryPC’s pricing alongside competitors’ offerings. This visual aid can help users make direct comparisons and assess the value proposition of each solution.
- Customer Testimonials: Incorporate images of customer testimonials or reviews discussing SentryPC’s pricing and value proposition. Authentic testimonials can provide credibility and reassurance to potential users.
Key Takeaways:
- Flexibility: SentryPC offers flexible pricing options, including monthly and annual subscription plans, to accommodate varying user requirements.
- Value Proposition: When evaluating SentryPC’s pricing, consider not only the cost but also the value provided in terms of features, customer support, and overall user experience.
- Comparison: Conduct a thorough comparison of SentryPC’s pricing with similar products in the market to ensure you’re getting the best value for your investment.
Ultimately, selecting the right monitoring solution involves weighing factors beyond just pricing, such as features, reliability, and customer support. By considering these factors holistically, users can choose a monitoring solution that meets their needs and provides long-term value for their investment.
Conclusion
Pricing is a critical factor to consider when selecting a monitoring solution like SentryPC. By understanding the pricing structure and comparing it with competitors, users can make informed decisions that align with their monitoring needs and budgetary constraints.
Features
When choosing a monitoring solution like SentryPC, evaluating the features it offers is crucial to ensure it meets your monitoring needs effectively. In this section, we’ll explore the key features of SentryPC and how they compare to other similar products in the market.
Key Features of SentryPC:
- Activity Monitoring: SentryPC provides comprehensive activity monitoring capabilities, allowing users to track and monitor user activity in real-time. This includes monitoring websites visited, applications used, keystrokes typed, and files accessed.
- Content Filtering: SentryPC offers robust content filtering tools, enabling users to block access to inappropriate websites and content categories. Users can customize filtering rules based on specific keywords, URLs, or content types to enforce safe browsing habits.
- Time Management: SentryPC includes time management features that allow users to set limits on computer usage. Users can define specific time periods during which the computer can be accessed, helping to prevent excessive screen time and promote productivity.
- Remote Control: SentryPC enables remote control capabilities, allowing users to remotely access and manage monitored devices. This feature is particularly useful for parents or employers who need to supervise computer usage from a distance.
- Alerts and Notifications: SentryPC provides customizable alerts and notifications to keep users informed about suspicious or unauthorized activities. Users can receive alerts via email or text message when predefined thresholds or triggers are met.
- Stealth Mode: SentryPC offers a stealth mode option, allowing users to monitor computer activity discreetly. This feature operates silently in the background without alerting users to its presence, ensuring covert monitoring when necessary.
Comparison with Competitors:
In comparing SentryPC’s features with other monitoring solutions in the market, users should consider factors such as:
- Comprehensiveness: Assess the breadth and depth of features offered by SentryPC relative to competitors. Look for solutions that provide a comprehensive set of monitoring and management tools to meet diverse user needs.
- Ease of Use: Evaluate the user interface and usability of SentryPC‘s features compared to other products. Choose a solution that offers intuitive controls and streamlined workflows for efficient monitoring and management.
Conclusion
Features are the backbone of any monitoring solution, and choosing the right set of features is essential for meeting your monitoring needs effectively. In this section, we’ve explored the key features of SentryPC and how they compare to other similar products in the market.
Compatibility
Compatibility is a crucial aspect to consider when choosing a monitoring solution like SentryPC. Ensuring that the software is compatible with your devices and operating systems is essential for seamless integration and optimal performance. Let’s explore the compatibility of SentryPC and how it stacks up against other similar products.
Device Compatibility:
SentryPC is designed to be compatible with a wide range of devices, including:
- Windows PCs: SentryPC is primarily designed for Windows-based computers, offering comprehensive monitoring and management features for Windows 10, 8, 7, and Vista.
- Mac Computers: While SentryPC is not compatible with Mac operating systems, there are alternative monitoring solutions available for macOS users seeking similar functionality.
Operating System Compatibility:
SentryPC is compatible with various Windows operating systems, including:
- Windows 10: SentryPC is fully compatible with Windows 10, the latest version of the Windows operating system, ensuring users can leverage the software’s features on their Windows 10 devices.
- Windows 8/7/Vista: SentryPC also supports older versions of the Windows operating system, including Windows 8, 7, and Vista, providing backward compatibility for users with legacy devices.
Browser Compatibility:
SentryPC‘s monitoring features are browser-agnostic, meaning they are compatible with most web browsers commonly used on Windows operating systems, including:
- Google Chrome: SentryPC supports monitoring activities performed on Google Chrome, one of the most popular web browsers globally.
- Mozilla Firefox: Users can also monitor activities conducted on Mozilla Firefox, another widely used web browser compatible with SentryPC‘s monitoring capabilities.
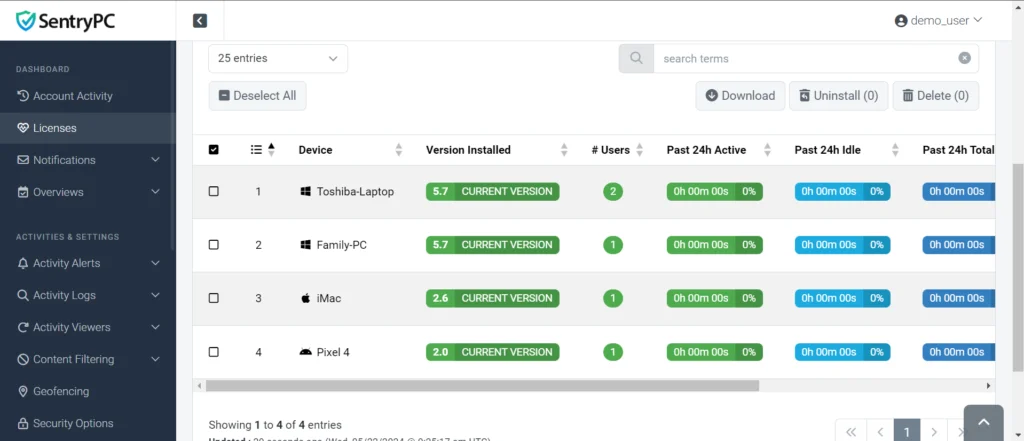
- Device Compatibility: Include images showcasing SentryPC‘s compatibility with various Windows-based devices, such as desktop computers, laptops, and tablets.
- Operating System Compatibility: Provide screenshots or visual representations of SentryPC‘s compatibility with different versions of the Windows operating system, including Windows 10, 8, 7, and Vista.
- Browser Compatibility: Showcase images of SentryPC‘s monitoring features in action on different web browsers, such as Google Chrome and Mozilla Firefox. These visuals can help users visualize how the software integrates with their preferred browser for monitoring purposes.
User Interface
In the realm of software development and design, the user interface (UI) stands as a critical element, shaping the interaction between users and digital systems. Let’s delve into what a user interface entails, its key components, and its pivotal role in enhancing user experiences across various platforms.
Understanding User Interface (UI):
What is a User Interface?
A user interface (UI) serves as the point of interaction between users and digital devices or software applications. It encompasses the visual elements, controls, and functionalities that enable users to navigate, interact with, and manipulate digital content or services. UI design focuses on creating intuitive, aesthetically pleasing interfaces that facilitate seamless user interactions and enhance usability.
Key Components of UI:
- Visual Design: Visual design elements, such as layout, typography, color schemes, and imagery, contribute to the aesthetic appeal and overall look and feel of the interface.
- Interactive Elements: Interactive elements, including buttons, menus, forms, and widgets, enable users to perform actions, input data, and navigate through the interface.
- Information Architecture: Information architecture encompasses the organization, structure, and labeling of content within the interface to facilitate easy navigation and access to relevant information.
- Feedback Mechanisms: Feedback mechanisms, such as visual cues, animations, and notifications, provide users with real-time feedback about their interactions, actions, or system status.
- Accessibility Features: Accessibility features ensure that the interface is usable by individuals with diverse abilities and disabilities, including considerations for screen readers, keyboard navigation, and color contrast.
Importance of UI:
- Enhanced Usability: A well-designed UI enhances usability by simplifying complex tasks, minimizing cognitive load, and guiding users through intuitive navigation paths.
- Improved User Satisfaction: Intuitive interfaces with visually appealing designs and seamless interactions contribute to positive user experiences, fostering user satisfaction and loyalty.
- Increased Engagement: Engaging UI designs that incorporate interactive elements and feedback mechanisms encourage user engagement and drive user retention.
- Brand Identity: UI design plays a crucial role in shaping the brand identity and perception of products or services, reflecting the brand’s values, personality, and visual identity.
- Competitive Advantage: In today’s competitive landscape, a superior UI can serve as a key differentiator, attracting users, and gaining a competitive edge in the market.
- Visual Design: Adding images showcasing visually appealing UI designs, color schemes, and typography can exemplify the importance of visual aesthetics in UI design.
- Interactive Elements: Including screenshots or illustrations of interactive elements like buttons, forms, or menus can elucidate how users interact with the interface.
- Accessibility Features: Incorporating images demonstrating accessibility features, such as screen reader compatibility or keyboard navigation, underscores the importance of inclusive design practices.
Conclusion:
User interface design plays a pivotal role in shaping user experiences, influencing usability, engagement, and brand perception. By prioritizing intuitive design principles, incorporating interactive elements, and ensuring accessibility, organizations can create compelling user interfaces that resonate with their target audience, drive user satisfaction, and propel business success.
Security
Security stands as a paramount concern in today’s interconnected digital landscape, where threats to data, systems, and privacy loom large. Let’s delve into the multifaceted realm of security, exploring its importance, key components, and strategies for mitigating risks effectively.
Understanding Security:
What is Security?
Security encompasses a range of measures and practices designed to protect digital assets, including data, systems, networks, and applications, from unauthorized access, breaches, and malicious activities. It entails implementing robust defenses, monitoring for potential threats, and responding promptly to security incidents to safeguard against vulnerabilities and mitigate risks.
Key Components of Security:
- Access Control: Access control mechanisms, such as authentication, authorization, and encryption, restrict access to sensitive data and resources based on user identities and permissions.
- Network Security: Network security measures, including firewalls, intrusion detection systems (IDS), and virtual private networks (VPN), safeguard network infrastructure from unauthorized access, malware, and cyber attacks.
- Data Protection: Data protection strategies, such as encryption, data masking, and data loss prevention (DLP) technologies, ensure the confidentiality, integrity, and availability of sensitive data throughout its lifecycle.
- Endpoint Security: Endpoint security solutions, such as antivirus software, endpoint detection and response (EDR) tools, and mobile device management (MDM) systems, protect individual devices from malware, unauthorized access, and data exfiltration.
- Security Monitoring and Incident Response: Continuous security monitoring, coupled with incident response procedures and threat intelligence, enables organizations to detect, analyze, and mitigate security incidents in a timely manner.
Importance of Security:
- Protection Against Threats: Security measures defend against a myriad of threats, including malware, phishing attacks, ransomware, and insider threats, mitigating the risk of data breaches and financial losses.
- Compliance Adherence: Compliance with industry regulations and data protection laws, such as GDPR, HIPAA, and PCI DSS, ensures that organizations uphold legal and regulatory requirements, avoiding penalties and reputational damage.
- Preservation of Trust: By safeguarding the confidentiality, integrity, and availability of data and systems, robust security measures foster trust among customers, partners, and stakeholders, bolstering brand reputation and customer loyalty.
- Business Continuity: Effective security practices contribute to business continuity by minimizing disruptions caused by security incidents, ensuring uninterrupted operations, and safeguarding critical assets.
- Risk Management: Security measures form an integral part of risk management strategies, enabling organizations to identify, assess, and mitigate security risks proactively, thereby safeguarding business interests and investments.
Conclusion:
Security is a cornerstone of modern digital operations, essential for protecting against evolving cyber threats and preserving the integrity and trustworthiness of digital assets. By implementing robust security measures, adhering to best practices, and fostering a culture of security awareness, organizations can mitigate risks effectively, safeguard their interests, and uphold the trust of their stakeholders in an increasingly interconnected world.
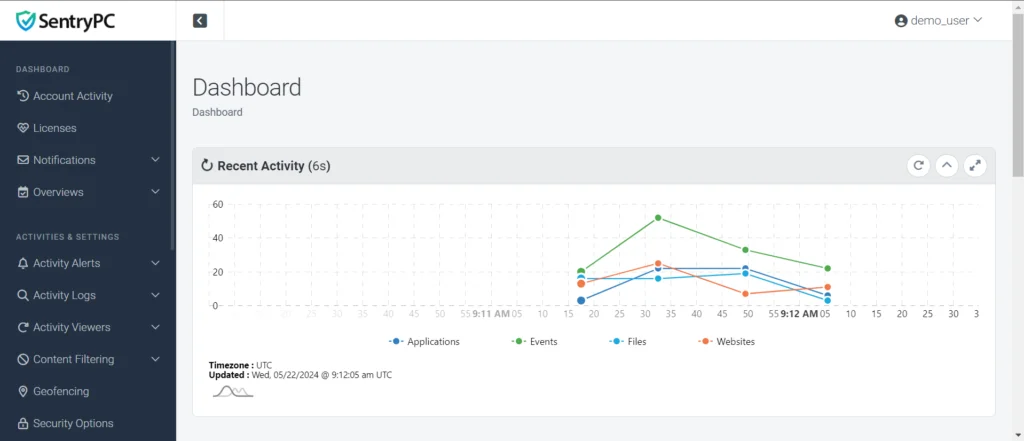
Monitoring Capabilities
In today’s digital landscape, monitoring capabilities play a pivotal role in safeguarding systems, networks, and data from threats. Whether in the realm of cybersecurity, infrastructure management, or performance optimization, effective monitoring empowers organizations to proactively identify, analyze, and mitigate potential risks. Let’s delve into the significance and applications of monitoring capabilities across various domains.
Understanding Monitoring Capabilities:
What are Monitoring Capabilities?
Monitoring capabilities refer to the suite of tools, technologies, and processes employed to observe, track, and analyze the performance and behavior of systems, networks, applications, or assets. These capabilities provide real-time insights into the operational status, security posture, and overall health of the monitored environment.
Key Components:
- Data Collection: Monitoring capabilities gather data from diverse sources such as logs, sensors, endpoints, and network traffic.
- Analysis and Alerting: Advanced algorithms analyze the collected data to detect anomalies, deviations from normal behavior, or potential security breaches. Alerts are generated to notify stakeholders about critical events.
- Visualization and Reporting: Data is presented in visually intuitive dashboards and reports, enabling stakeholders to comprehend complex information at a glance.
- Response and Remediation: Monitoring capabilities facilitate timely responses to security incidents or performance issues through automated actions or predefined workflows.
Applications Across Domains:
- Cybersecurity: In the realm of cybersecurity, monitoring capabilities are indispensable for threat detection, incident response, and compliance adherence. By continuously monitoring network traffic, system logs, and user activities, organizations can detect suspicious behavior indicative of cyber threats such as malware infections, unauthorized access attempts, or data breaches.
- Infrastructure Management: Monitoring capabilities play a vital role in managing the performance, availability, and capacity of IT infrastructure components such as servers, databases, and cloud services. Through proactive monitoring of resource utilization metrics, organizations can identify performance bottlenecks, predict capacity requirements, and optimize resource allocation to ensure seamless operations.
- Application Performance Monitoring (APM): APM solutions leverage monitoring capabilities to track the performance and user experience of web applications, mobile apps, or software services. By monitoring metrics like response time, error rates, and transaction throughput, organizations can pinpoint performance issues, optimize application performance, and enhance user satisfaction.
Conclusion:
Monitoring capabilities serve as a linchpin in modern-day security and operational strategies, enabling organizations to preemptively address threats, optimize performance, and ensure regulatory compliance. By harnessing the power of advanced monitoring tools and techniques, organizations can fortify their defenses, enhance resilience, and stay ahead in the ever-evolving threat landscape.
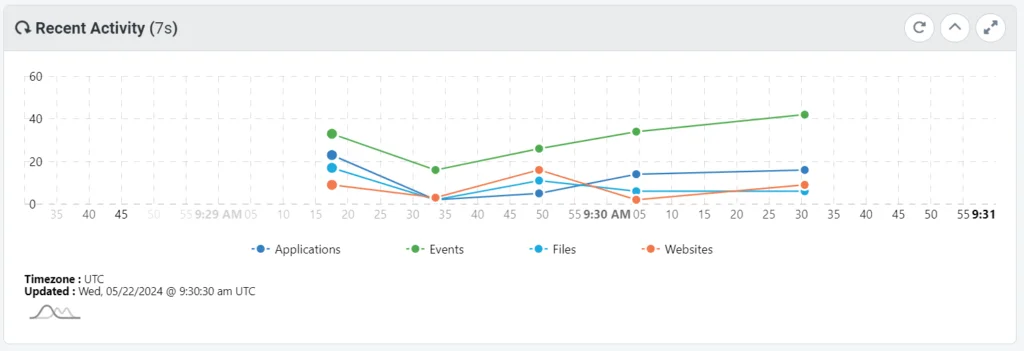
Reporting and Analytics
Reporting and analytics serve as indispensable tools in today’s data-driven business landscape, enabling organizations to glean actionable insights, make informed decisions, and drive performance improvements. Let’s explore the significance of reporting and analytics, their key components, and how they empower organizations to unlock the value of their data.
Understanding Reporting and Analytics:
What are Reporting and Analytics?
Reporting involves the process of organizing and presenting data in a structured format, typically in the form of tables, charts, or graphs, to convey information and trends. Analytics, on the other hand, involves the exploration, interpretation, and visualization of data to uncover patterns, correlations, and actionable insights that inform decision-making and drive business strategies.
Key Components:
- Data Collection and Integration: Reporting and analytics rely on the collection and integration of data from various sources, including databases, applications, and external sources, to create a comprehensive view of organizational performance.
- Data Analysis: Analytics involves the application of statistical techniques, data mining, and machine learning algorithms to analyze large datasets and extract meaningful insights, trends, and patterns.
- Visualization: Visualization tools and techniques, such as dashboards, charts, and interactive graphs, enable users to visualize complex data sets in a comprehensible and intuitive manner, facilitating data-driven decision-making.
- Predictive Modeling: Predictive analytics leverages historical data and statistical algorithms to forecast future trends, identify potential risks, and optimize business processes, enabling proactive decision-making and strategic planning.
- Reporting and Distribution: Reporting functionalities enable users to generate and customize reports tailored to specific requirements, formats, and stakeholders, disseminating insights and information across the organization effectively.
Importance of Reporting and Analytics:
- Informed Decision-Making: Reporting and analytics provide decision-makers with timely, accurate, and actionable insights, enabling informed decision-making across various functions, including finance, marketing, operations, and strategic planning.
- Performance Optimization: By analyzing key performance indicators (KPIs) and performance metrics, organizations can identify areas of improvement, optimize processes, and enhance operational efficiency and effectiveness.
- Customer Insights: Analytics enables organizations to gain deeper insights into customer behavior, preferences, and satisfaction levels, empowering them to tailor products, services, and marketing strategies to meet customer needs and preferences.
- Risk Management: Predictive analytics helps organizations identify and mitigate potential risks, such as market fluctuations, supply chain disruptions, or cybersecurity threats, minimizing potential losses and maximizing opportunities.
- Competitive Advantage: Leveraging reporting and analytics capabilities allows organizations to gain a competitive edge by identifying market trends, understanding competitor strategies, and capitalizing on emerging opportunities in a dynamic business environment.
Conclusion:
Reporting and analytics serve as catalysts for organizational success, empowering decision-makers with actionable insights, driving performance improvements, and fostering innovation and competitiveness. By harnessing the power of data through robust reporting and analytics capabilities, organizations can unlock new opportunities, mitigate risks, and achieve their strategic objectives in an increasingly data-driven world.
Support and Customer Service
Support and customer service play a pivotal role in shaping customer experiences and fostering long-term relationships between businesses and their clientele. Let’s explore the significance of support and customer service, their key components, and how they contribute to customer satisfaction and loyalty.
Understanding Support and Customer Service:
What is Support and Customer Service?
Support and customer service encompass the range of services, assistance, and resources provided by businesses to address customer inquiries, resolve issues, and ensure customer satisfaction. It involves proactive engagement with customers before, during, and after purchase, aiming to meet their needs, exceed their expectations, and build lasting relationships.
Key Components:
- Multichannel Support: Support and customer service are delivered through various communication channels, including phone, email, live chat, social media, and self-service portals, to provide customers with multiple avenues for seeking assistance.
- Timely Response: Timely and responsive support is essential for addressing customer inquiries and issues promptly, minimizing wait times, and demonstrating a commitment to customer satisfaction.
- Empathetic Communication: Effective customer service entails empathetic communication, active listening, and understanding customer concerns, emotions, and preferences to deliver personalized and tailored assistance.
- Problem Resolution: Resolving customer issues efficiently and effectively is crucial for restoring customer confidence, mitigating dissatisfaction, and fostering trust and loyalty.
- Continuous Improvement: Continuous monitoring, feedback collection, and performance analysis enable organizations to identify areas for improvement, refine support processes, and enhance the overall customer service experience.
Importance of Support and Customer Service:
- Customer Satisfaction: Responsive and empathetic customer service enhances satisfaction levels, fosters positive experiences, and strengthens customer loyalty and advocacy.
- Brand Reputation: Exceptional customer service contributes to a positive brand reputation, as satisfied customers are more likely to recommend the brand to others and become loyal advocates.
- Retention and Loyalty: By providing excellent support and customer service, businesses can retain existing customers, reduce churn rates, and increase customer lifetime value.
- Competitive Differentiation: Superior customer service can serve as a key differentiator in a competitive market, attracting customers and setting businesses apart from competitors.
- Business Growth: Positive customer experiences lead to repeat purchases, referrals, and organic growth, driving revenue and profitability for the business in the long run.
- Customer Interactions: Adding images of customer service representatives assisting customers through various channels, such as phone calls, live chat, or email, can illustrate the diverse touchpoints of customer support.
- Customer Feedback: Incorporating visuals of feedback forms, customer satisfaction surveys, or testimonials can highlight the importance of feedback in driving continuous improvement and enhancing the customer service experience.
- Problem Resolution: Including images depicting satisfied customers or resolved issues can exemplify the impact of effective problem resolution on customer satisfaction and loyalty.
Conclusion:
Support and customer service serve as cornerstones of customer-centric businesses, playing a crucial role in delivering exceptional experiences, building customer trust, and driving long-term success. By prioritizing responsive communication, empathetic assistance, and continuous improvement, organizations can create meaningful connections with customers, foster loyalty, and differentiate themselves in a competitive marketplace.
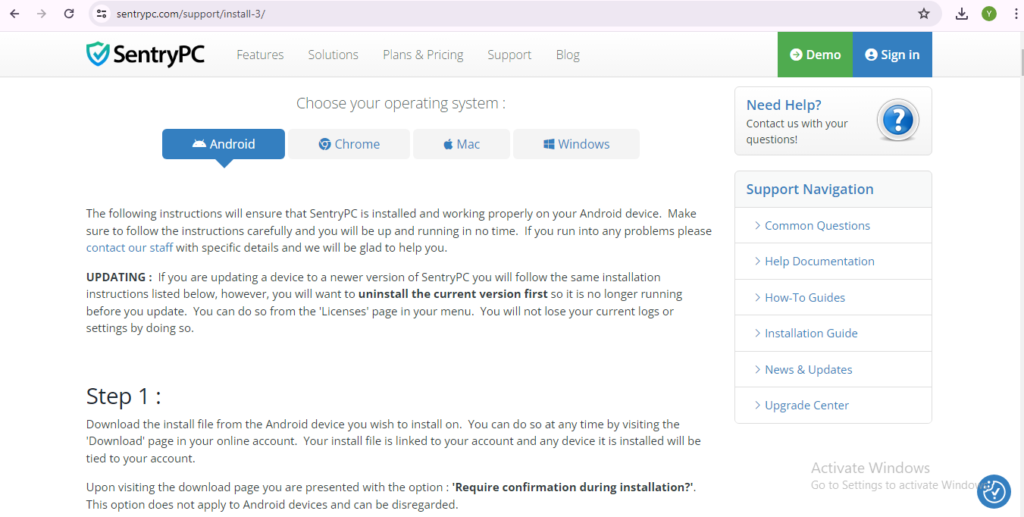
Installation and Setup
Installing and setting up SentryPC is a straightforward process designed to get you up and running quickly. Whether you’re a tech-savvy individual or a beginner, SentryPC provides a seamless installation experience. Here’s a step-by-step guide to help you through the process:
- Downloading the Software
- To begin, visit the official SentryPC website and download the installation file. Ensure you download the correct version compatible with your operating system.
- Running the Installer
- Once the download is complete, open the installer file to start the installation process. Follow the on-screen prompts to proceed through the setup wizard.
- Accepting the License Agreement
- During the installation, you will be prompted to read and accept the license agreement. It’s important to review the terms and conditions before proceeding.
- Choosing the Installation Location
- The installer will ask you to choose the location where SentryPC will be installed. You can select the default location or specify a different directory according to your preference.
- Configuring Initial Settings
- After installation, you will be guided through the initial setup. This includes creating an administrator account and setting up a secure password to protect access to SentryPC.
- Installing on Additional Devices
- If you need to monitor multiple devices, SentryPC allows you to install the software on each device you wish to monitor. Follow the same installation steps for each additional device.
- Remote Installation Option
- SentryPC offers a remote installation option, enabling you to install the software on other devices without physical access. This is particularly useful for managing a network of computers in different locations.
- Configuring Monitoring and Control Settings
- Once installed, you can configure the monitoring and control settings according to your needs. This includes setting up activity tracking, website blocking, time management, and more.
- Connecting to the Dashboard
- After configuration, connect to the SentryPC dashboard using your administrator credentials. This is where you can manage and monitor all connected devices from a single interface.
- Testing the Setup
- It’s a good idea to test the setup by performing some monitored activities and checking if SentryPC records them accurately. This ensures that everything is working correctly before full deployment.
pros and cons
Pros:
- Comprehensive Monitoring: SentryPC offers extensive monitoring capabilities, allowing users to track various aspects of computer usage, including websites visited, applications used, keystrokes typed, and more. This comprehensive monitoring can provide valuable insights into user behavior and productivity.
- Activity Logging: The software logs all user activities, providing detailed reports that can be useful for analyzing productivity trends, identifying potential security risks, or enforcing compliance with company policies.
- Content Filtering: SentryPC enables users to block access to specific websites or applications, helping to prevent distractions, enforce internet usage policies, or protect against inappropriate content.
- Remote Management: SentryPC can be managed remotely, allowing administrators to monitor and control multiple computers from a centralized dashboard. This feature is particularly beneficial for businesses with distributed teams or parents managing multiple devices.
- Customizable Alerts: Users can set up customizable alerts to receive notifications when certain predefined events occur, such as attempts to access blocked websites or applications.
Cons:
- Privacy Concerns: The extensive monitoring capabilities of SentryPC may raise privacy concerns among users, particularly in a workplace environment where employees may feel that their privacy is being invaded.
- Resource Intensive: SentryPC may consume significant system resources, particularly when running in the background and continuously monitoring user activities. This could potentially impact the performance of the monitored computers.
- Limited Compatibility: SentryPC may not be compatible with all operating systems or devices, limiting its usefulness in environments with diverse hardware and software configurations.
- Complex Setup: Setting up and configuring SentryPC to meet specific monitoring and control requirements may require a certain level of technical expertise. Users may need to invest time and effort into understanding the software’s features and settings.
- Cost: SentryPC is a paid software solution, and the cost may be a consideration for budget-conscious users, particularly for larger deployments or organizations with multiple users.
Conclusion
SentryPC offers a robust suite of features for monitoring and controlling computer usage, making it a valuable tool for businesses, educational institutions, and parents seeking to manage and protect their digital assets. With comprehensive monitoring capabilities, customizable alerts, and remote management functionality, SentryPC provides users with the tools they need to track user activities, enforce policies, and maintain security.
However, users should be mindful of potential privacy concerns, as the extensive monitoring capabilities of SentryPC may infringe upon individual privacy rights, particularly in workplace environments. Additionally, the software’s resource-intensive nature and compatibility limitations may pose challenges for some users.
Despite these considerations, SentryPC remains a viable solution for organizations and individuals looking to maintain productivity, enforce compliance, and protect against security threats in today’s digital age. By carefully evaluating its features, benefits, and limitations, users can make informed decisions about whether SentryPC is the right fit for their monitoring and control needs.
